SHA-1 SSL Signatures in Your SSL Certificates
The SHA-1 cryptographic hash algorithm is twenty years old, and the feasibility of collision attacks against it is improving. To combat that threat, Google Chrome will start marking connections as insecure if the website uses a SHA-1 signed SSL certificate.
Starting in version 42 of Chrome, websites using a SHA-1 signed SSL certificate will get a red X across the lock, and users will be notified their connection might not be private. Mozilla plans to make similar changes to Firefox.
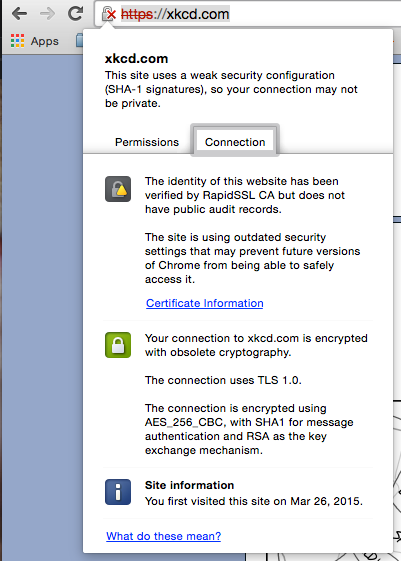
Currently, Google Chrome stable is version 41, Chrome Beta is version 42, and Canary builds are version 44. As each stable release of chrome is pushed on six week intervals, the stable version of Chrome is going to be updated to version 42 in the next few weeks.
At this time, only SHA-1 certificates with a validation date expiring after 2015 will be marked as insecure. To stay ahead of the curve, Engine Yard is going to be reaching out to all customers affected by this change.
If you’re doing this on your own, the easiest way to fix this issue is by updating the older certificates to use SHA-2. If interested, you can use a third party to scan your existing certificate for any other shortcomings. Qualys does a pretty good job, as does DigiCert and Symantec.
If you have questions about the security procedures or controls in place at Engine Yard, please do not hesitate to contact us.
You can reach us via our ticketing system or in #engineyard on Freenode.

















Share your thoughts with @engineyard on Twitter